This is Part 3 of a series on Security & Privacy for Mobile Apps.
Part 1 of this series introduced main concepts related to security on mobile apps. Part 2 went deeper into the security elements and guidelines related to security and privacy on mobile applications. In this Part 3, I will cover security from the PCI compliance perspective.
Handling Personal or Sensitive Information
Personal and sensitive information include any information that is critical for a user, for example credit card numbers, credit card validation codes, social security numbers, driver’s license numbers, name, addresses and date of birth, and other Personally Identifiable Information (PII). Any such information must be properly handled and secured.
When dealing with credit cards in particular, you may have to adhere to strict security requirements such as the ones as defined by the Payment Card Industry Security Standards Council, or PCI for short. The PCI council defined a number of requirements and certification to help to ensure both devices and software applications all take the proper steps to protect cardholder data. The PCI council consists of the following companies: American Express, Discover Financial Services, JCB International, MasterCard Worldwide and Visa Inc.
Even if your application is not handling cardholder information, the requirements by the PCI council are good guidelines to follow if your mobile (web) application deals with personal sensitive information of any kind.
PCI Data Security Standard (DSS) requirements
Let’s take a look at the PCI Data Security Standard (DSS) requirements. These requirements apply to “any entity that stores, processes, and/or transmits cardholder data.” In short, “if your business accepts or processes payment cards, it must comply with the PCI DSS.” Note that “to comply”, means that the payment application must pass a PCI-provided assessment.
Table 1: Payment Application DSS Requirement
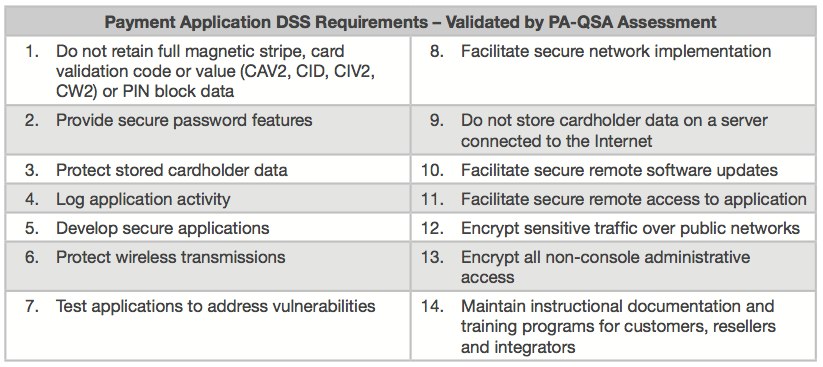
Source: Payment Card Industry Security Standards
The PCI Data Security Standard defines fourteen (14) requirements — some technical while other operational — that affect both the server-side and client/mobile-side of the payment application. Let’s cover each of these requirements in some more detail:
1. Do not retain full magnetic stripe, card validation code or value or PIN block data
How to: Always prompt for such information; never store locally on the device. Always prompt for PIN.
2. Provide secure password features
How to: Always prompt for PIN before allowing access to the app’s critical paths or sensitive information. Use the PIN to secure application data.
3. Protect stored cardholder data
How to: Do not store cardholder information on the device. Tokenize access to critical information (tokens are covered below). Use the PIN to secure application data.
4. Log application activity
How to: Keep a local log of critical activities, such as when user logs into the application, performs a purchase, and so on. This typically is a circular log. Provide the means to remotely access or upload the log as needed.
5. Develop secure applications
How to: Design and implement the mobile application with security in mind. Do this by implementing the different requirements being discussed in this article.
6. Protect wireless transmissions
How to: Perform all communication over an encrypted secure connection (typically over HTTPS/TLS).
7. Test applications to address vulnerabilities
How to: Implement a robust test-suite that includes automated and manual testing that validates that no access to critical application paths is possible unless the user authorizes it via a PIN, that API calls and data over network connections is in fact being encrypted, that no credit card information is stored locally, and that any personal information stored in local data is properly encrypted.
8. Facilitate secure network implementation
How to: See #6 above
9. Do not store cardholder data on a server connected to the Internet
How to: Design a network architecture that separates production systems from the public Internet. Deploy production servers with critical/personal information behind a firewall.
10. Facilitate secure remote software updates
How to: Only trust software updates from trusted sources. Leverage app stores/markets and app signing for native applications. Leverage centralized approach of mobile web apps. Perform all software updates over a secure network connection.
11. Facilitate secure remote access to application
How to: See #10. In addition, see #6 — all remote/network communication shall only be done over secure network connections.
12. Encrypt sensitive traffic over public networks
How to: See #6 above
13. Encrypt all non-console administrative access
How to: See #4 and #6 and #10. All access to secure data, administrative or not, shall be done over secure connections.
14. Maintain instructional docs and training programs for customers, resellers and integrators
How to: From the mobile application perspective, provide FAQ and Help pages that describe the privacy and security aspects of the application. Include Privacy terms and conditions.
Other PCI Information and/or Requirements
The following two tables show the general PCI goals vs. requirements, and PIN-entry device security requirements.
Table 2: PCI Data Security Standard (DSS) requirements
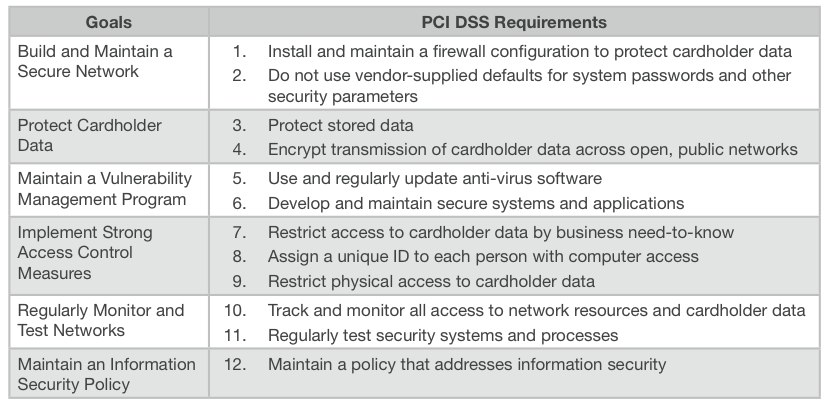
Source: Payment Card Industry Security Standards
Note that most of these requirements on Table 2 were covered on the previous section.
Table 3: PCI PIN Entry Device Security Requirements
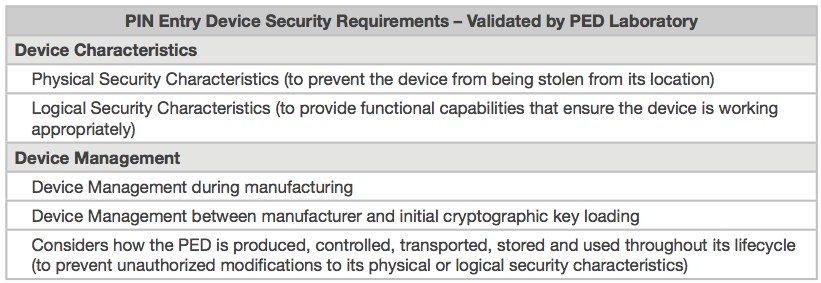
Source: Payment Card Industry Security Standards
And these requirements on Table 3 are related to physical devices, in particular device characteristics and management requirements.
Conclusion
On this 3-part series we have covered security on mobile applications – introduction, elements and guidelines for secure mobile apps, and PCI requirements for mobile payment applications. At the end, it is about protecting the user by protecting related critical information –credit card numbers, credit card validation codes, social security numbers, driver’s license numbers, name, addresses and date of birth, and other Personally Identifiable Information (PII); all such information must be properly handled and secured.
As privacy continues to become more critical over time, with the number of apps exponentially increasing, and with potential legislation in the future, having clear privacy and security implementation, wording/messaging and responsibilities are all very important.
Finally, as product owners and developers, we are all responsible for properly implementing our mobile applications and protecting the user…
Resources